Guide Mozilla Thunderbird
The following recommendations can help to take measures to detect unwanted and dangerous e-mail messages and to protect stored passwords and the network connections to the e-mail server. As a representative of other email clients, only Mozilla Thunderbird is considered here in the standard configuration. Although not all of the measures described can be implemented in individual cases in other clients, these recommendations can be used as a checklist.
Most of the recommended settings are not accessible via the normal user interface. Use the "configuration editor" for this purpose (Instructions).
In Thunderbird, the settings described here can help to identify forged sender addresses.
Show full e-mail address of the sender:
mail.showCondensedAddresses = false
Display sender information in the SENDER field from the email header, if different from the FROM, to detect possible sender spoofing:
mailnews.headers.showSender = true
For the structured presentation of content such as text, images and hyperlinks, senders can use the HTML format, although it was not originally intended for use in e-mails. In order to be able to display such content correctly, many email clients are equipped with functions similar to those of browsers. In principle, this also gives rise to the same security and privacy problems as with web browsers. With the default settings, every modern email client (such as Thunderbird) should block the execution of scripts or active content and the reloading of external content. What is not prevented, however, is the malicious concealment of links in HTML e-mails.
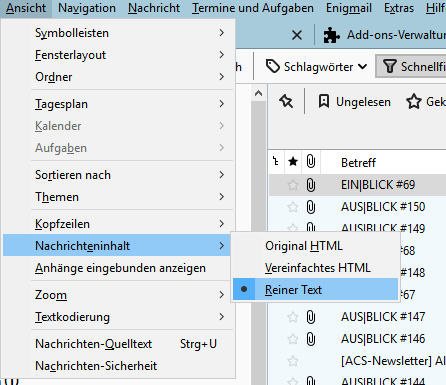
Received messages should always be displayed as text (i.e. not in HTML format):
View → Message Content → Plain Text
If, however, an HTML e-mail becomes completely incomprehensible because it is displayed as text, it is always possible to switch to the HTML view in the same way.
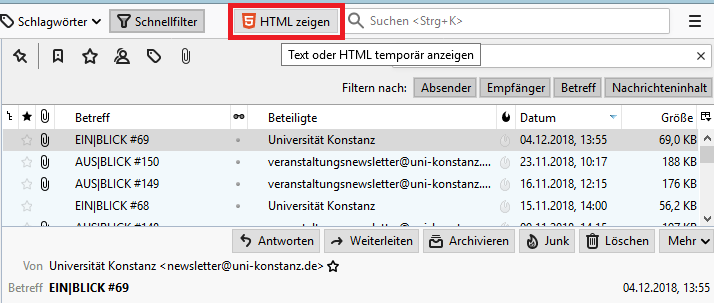
To simplify switching between HTML and text view, there is the extension Allow HTML Temp for Thunderbird (installation instructions). This enables the addition of a button labelled "Show HTML", which displays the selected message once in the original HTML format and automatically returns to the text view when switching to the next message.
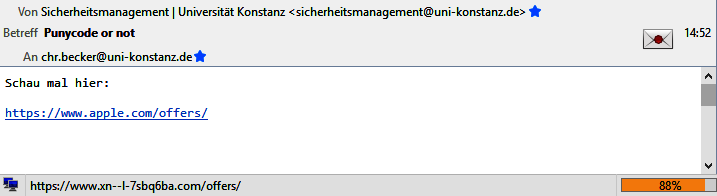
Internationalised domain names as link targets offer another possibility for disguise. The so-called punycode representation for internationalised domain names makes it easier to recognise possible domain spoofing:
network.IDN_show_punycode = true
The option "Show attachments included" should be deactivated in order not to automatically open dangerous attachments for display when reading an (HTML) e-mail and to avoid infection with viruses:
mail.inline_attachments = false
Thunderbird automatically prevents the reloading of graphics. The execution of Javascript from "Remote Content" in HTML e-mails should also be deactivated:
javascript.enabled = false
Stored passwords for access to SMTP and IMAP servers should be protected from unauthorised persons with a master password (instructions).
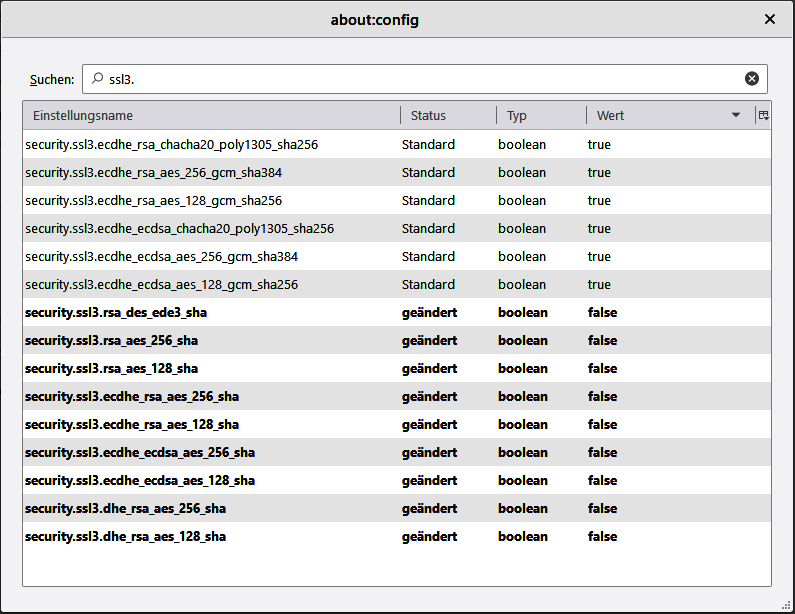
The BSI's Technical Guideline TR-02102-2 recommends only using TLS with protocol version 1.2 or higher with the cipher suites listed there. This is achieved with the following settings:
security.tls.version.min = 3 /^security.ssl3.*sha[^\d]/ = false (vgl. Bild) security.pki.sha1_enforcement_level = 1
Although the cipher suites with CHACHA20-POLY1305 from D. J. Bernstein are not included in the BSI recommendations, we also classify them as secure, so they do not need to be deactivated.
Prohibit insecure re-negotiation (can cause problems):
security.ssl.require_safe_negotiation = true security.ssl.treat_unsafe_negotiation_as_broken = true
Enforce strict certificate pinning (HPKP) (e.g. for add-on updates):
security.cert_pinning.enforcement_level = 2
Communication and Information Centre (kiz)
Please contact us if you have questions or problems related to the kiz services:
Office hours
Monday - Thursday
09:00 h - 12:00 h and 13:00 h - 15:30 h
Friday 09:00 h - 12:00 h
Phone
+49 (0) 731 / 50 - 30000
Telefax
+49 (0) 731 / 50 - 1230000
Order a Callback
helpdesk(at)uni-ulm.de
Support Portal (Uni internal)
[more]
Service Points are locations where you can visit us personally.
Using self-service functions of the Identity Management System (IDM): Administer permissions, subscribe to services, change passwords.
Research in the library stock: monographs, textbooks, magazines, university publications, e-books, e-journals, national licenses, and the contents of the institutional repository OPARU.
With about 400 keywords you will get direct access to our services. If something isn't listed, please contact our Internet Editorial Office.